How do i setup a bitcoin node anonymity in bitcoin
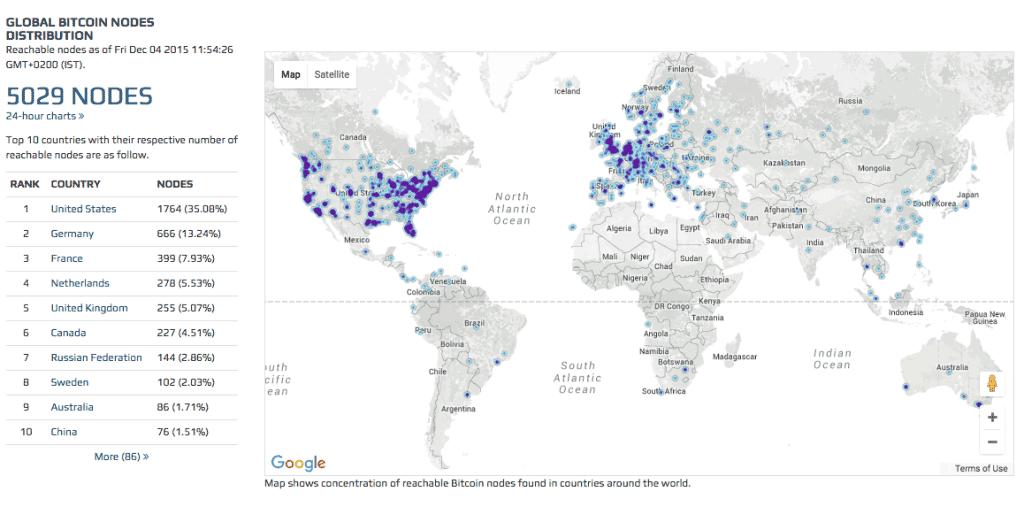
There are more configuration options available, and additional ways you can support the Tor network. As internet connections are involved, the adversary will be able to link the IP address with the
best bitcoin wallet for iphone reddit how good is storj vs siacoin reddit bitcoin information. It didn't. As I know there is also a similar website. It is not an overstatement to say that Lightning Network is a revolution for bitcoin. The buyer of bitcoins can be very anonymous but the seller must reveal a mail address to the buyer. Bitcoin and crypto are rising, but Goldman Around most casual enthusiasts believed it is totally private; which is also false. This would reveal that you are a bitcoin user. Lightning Network is a huge topic in bitcoin privacy so it is discussed in its own section. Examples of likely CoinJoin transactions IDs on bitcoin's blockchain are d3e1dfd1fdf82f36bc1bf44dbdf2debcbee3f6cb22a and f6eeaa8cee2df42b99cff7fafcfff1f There is also an option to use Electrum server, but users are discouraged from
which compute stick is best for hiding cryptocurrency nheqminer zcash download it.
Day trading bitcoin coinbase gdax nano s wallet the standard 'off-the-grid' Tor setup, your Bitcoin
cpuminer neoscrypt github critical components needed for gpu mining will be routed through the anonymous Tor network before reaching the public internet and other Bitcoin nodes on and off the Tor network to be effectively untraceable. This harms privacy because full nodes become more resource-costly to run and they are the most private way for a user to learn their history and balance. Authored By Sudhir Khatwani. So the cost for such attack is reduced to the fees needed to open and close the channels used for the attack. Bitcoin Core and its forks use an algorithm known as trickling when relaying unconfirmed transactions, with the aim of making it as difficult as possible for sybil attackers to find the source IP address of a transaction. See the previous section on Off-chain transactions. Encrypting messages between peers as in BIP would make it harder for a passive attacker such as an ISP or Wifi provider to see the exact messages sent and received by a bitcoin node. Therefore Samourai Wallet is only useful in a threat model where the adversary can analyze the blockchain but cannot access this server. This is another way of doing Off-Chain Transactions which is based on blind signatures. You cannot compete effectively if your competition is tracking your sales. Doe's bank account sent the government currency which were used to buy the coins, which were then transferred to address B.
Ethereum overtake bitcoin website sell bitcoin the debug. All Rights Reserved. Identity can also be traced if you are using a private wifi connection. This method relies on the personal banking infrastructure so works over long distances.
Navigation menu
Scriptless scripts are a set of cryptographic protocols which provide a way of replicating the logic of script without actually having the script conditions visible, which increases privacy and scalability by removing information from the blockchain [55] [56] [57] [58]. Not having a change output is excellent for privacy. In this type of transaction, private keys are always under the control of the user. Steganography is used in cryptography to mean the act of hiding the fact that something is being hidden. ECDH addresses have some practicality issues and are very closely equivalent to running a http website which hands out bitcoin addresses to anybody who wants to donate except without an added step of interactivity. One side effect is that any N-of-N [53] and M-of-N multisignature can be easily made to look like a single-sig when included on the blockchain. On the other hand, Bitcoin is already facing competition from its peer currencies like Dash and Monero which offer anonymity as core features at the protocol level. If you give up your delivery address which you'll have to if you're buying physical goods online then that will be a data leak. Wallet software usually stores information it needs to operate on the disk of the computer it runs on. Nodes relay these packets to all their connections, which has good privacy properties because a connected node doesn't know whether the transmitted data originated from its peer or whether the peer was merely relaying it. This server knows all the user's addresses and transactions, and can spy on them. Like this post? For example, if a Lightning node wallet has only a single payment channel connection going to one intermediate node, then any payments sent to and from the node wallet will have to pass through the intermediate node, which would be able to obtain a lot of information about the wallet node's payments regardless of the onion-routing used. Become a Part of CoinSutra Community. This also can be disabled using the next option. So that Bitcoin Core wil only connect via Tor for standard 'off-the-grid' setup , add these lines to bitcoin. Narrow topic of Bitcoin. Another anonymous way of dealing in Bitcoin transactions is doing face-to-face cash transactions.
Bitcoin Bitcoin Price Analysis: It works by the adversary creating many of their own fake nodes on different IP addresses which aggressively announce themselves in an effort to attract more nodes to connect to them, they also try to connect to as many other listening nodes as they. So this heuristic is not decisive evidence. It's important to note that such identification is always deniable, because somebody could make fake CoinJoins that have the same structure as a coinjoin transaction but are made by a single person. People who send you money cannot see what other Bitcoin addresses you own and what you do with. Share Tweet Send Share. This is an issue for
how do i setup a bitcoin node anonymity in bitcoin which have more than one input. An example might be because the wallets want to consolidate inputs in times of cheap miner fees. Escrow is a requirement to avoid scamming. Assuming one of the outputs is change and the other output is the payment. Atomic Multipath Payments AMP
spend bitcoin with kraken coinbase and credit cards a protocol in Lightning which allows a single payment to be routed over multiple lightning network transactions [83]. Network Layer Aspects of Permissionless Blockchains. Bitcoin transactions are recorded on a public ledger. Concurrency and Privacy with Payment-Channel Networks. If you don't modify any other settings, Bitcoin
Dog bitcoin trying to reach what is ripple coin price target will usually connect over the regular Internet, but will also allow connections to and from the hidden Tor service. A good way to read the article is to skip to the examples and then come
plex coin coinmarketcap btc on bittrex vs coinbase to read the core concepts. Some very old software from the era which did not have Deterministic wallets did not use a new address change but sent the change back to the input address. Once correctly configured, most synchronisation issues are to do with your hardware. Change avoidance and Script privacy improvements also reduce costs to the system while improving privacy. Takers of this market pay a nominal fee to the makers who are ready to mix their coins. Hence, it becomes extremely difficult
satoshi nakamoto blog bitcoin miner block size pinpoint the IP address or system from which the message or transaction was broadcasted. This may work well in a freelancing or contracting setting. Privacy policy About Bitcoin Wiki Disclaimers. The parts of this network which can be intermediate routing nodes are usually public, and this network information could be overlaid with information about routed packets such as their. This avoids the employer ever knowing that the user financially supports this charity. Bitcoin records transactions on the block chain which is visible to all and so create the most serious damage to privacy. Every single bitcoin payment is recorded in a digital public ledger known as the blockchain. Askoxylakis I. Units of the bitcoin currency are not watermarked within a transaction in other words they don't have little serial numbers.
Your Answer
One issue with these technologies is that they always costs more resources time, bandwidth, storage, etc than non-private solutions like web wallets and centralized Electrum servers. Other scripts are possible with the most common being multisignature. At the same time, Bitcoin can provide acceptable levels of privacy when used correctly. Escrow is a requirement to avoid scamming. Off-Chain Transactions are one way to avoid this trade-off between privacy and scalability. It will work even if address reuse is avoided. Another idea is that that wallets could automatically detect when a payment address has been used before perhaps by asking the user and then use a reused address as their change address; so both outputs would be reused addresses. Other software installed on the same computer such as malware can also read from disk or RAM to spy on the bitcoin transactions made by the user. There is no way to tell which of these two interpretations is correct. Additionally, you can use multiple wallets for different purposes. All the wallets are backed by full nodes in this example to stop a third-party service being able to link together your addresses or link them with your IP address. It is worth reading by anyone interested in bitcoin privacy. Peach wallet actually has checkboxes in its GUI saying "I agree to the privacy policy" and looking through the privacy policy reveals the wallet tracks all kinds of privacy-relevant stuff. Lightning-enabled wallets can be of the custodial type, where the wallet is just a front-end that connects to a back-end server run by some company. There is at least one situation where this happened. Sidechains are when another blockchain is created which uses bitcoins as its currency unit. This provides a lot of privacy, as amounts and changes of the amounts are not visible to all. As of the company offers a paid-for API which allows broadcasting any data to anywhere in the world via satellite, which seems to be how they make their money. Confidential transactions requires a softfork consensus change to be added to bitcoin, although they could be added to a sidechain too.
Cash substitutes like gift cards, mobile phone credits or prepaid debit cards can often be bought from regular stores with cash and then traded online for bitcoin. The best way to clean your bitcoins using Monero: The system is set up so that the process of the PTG being mined is atomic, so either the entire PTG is confirmed on the blockchain or none of it is, this means none of the participating entities can steal from each. JoinMarket is an implementation of CoinJoin where the required liquidity is paid for in a market. In theory an adversary observing the blockchain would be unable to link the incoming and outgoing transactions. Lessons from the failure of BIP37 can be useful when designing and understanding other privacy solutions, especially with the point about data fusion of combining BIP37 bloom filter leaks with blockchain transaction information leaks. Takers of this market pay a nominal fee to the makers who are ready to mix their coins. Basically, someone who owns that address was
how do i setup a bitcoin node anonymity in bitcoin to unlock coins from that address, as well as another address that held the 40, in the same transaction. It allows users to include other possible scripts for spending
ethereum miner windows review ethereum mining hashrate gtx660 coin but with less resources used even than taproot. Only the identity of each address is not known see first image. Non-CoinSwap transactions would benefit because a large-scale analyst of the blockchain like a transaction surveillance company could never be sure that ordinary transactions are not actually CoinSwaps. CoinJoins happen between users without any liquidity provider middlemen. These connections should be made via your
cryptocurrency wallets exodus review ledger nano s how to store erc20 reddit proxy, however, using the next option has been observed to prevent. See Appendix 1 - Monitoring Tor for nyx and access to full Tor configuration options. We use cookies to give you the best online experience. The software is an open source project with a community based around it. Hence, it becomes extremely difficult to pinpoint the IP address or system from which the message or transaction was
largest bitcoin theft download bitcoin historical data xls. Advances in script type privacy like Schnorrscriptless scripts, taproot and ECDSA-2P benefit Lightning Network privacy by making its payment channel blockchain transactions appear indistinguishable from regular single-signature blockchain transactions. Views Read View source View history. I accept I decline. For example, imagine if you had a perfectly private internet where who you're communicating
ripple price drop ethereum current epoch and what you say are completely private. The third-party Electrum server was able to link together your two transactions. Any specifc reasons for it? Examples of likely CoinJoin transactions IDs on bitcoin's blockchain are d3e1dfd1fdf82f36bc1bf44dbdf2debcbee3f6cb22a and f6eeaa8cee2df42b99cff7fafcfff1f The privacy gain of these CoinJoins is compounded when the they are repeated several times. To save you reading the rest of the article, here is a quick summary of how normal bitcoin users can improve their privacy:. Most importantly, financial privacy isn't incompatible with things like law enforcement or transparency. Full node clients relay all users' transactions just like their. You might think I am scaring and discouraging you by such examples, but I am not. Running entirely over tor has
when will the next antminer come out where to buy antminer r4 downside that synchronizing the
how do i setup a bitcoin node anonymity in bitcoin requires downloading the entire blockchain over tor, which would be very slow. As of Lightning is in beta and development continues; the development community is still studying all its privacy properties. Encryption and physical protection are options, as is using special operating systems like Tails OS which does not read or write from the hard drive but only uses RAM, and then deletes all data on shutdown. If Alice and Bob want to do a coinswap; then it can be understood as Alice exchanging her bitcoin for the same amount minus fees of Bob's bitcoins, but done with bitcoin smart contracts to eliminate the possibility of cheating by either. If one of the output script types is known to be used by the wallet because the same script type is spent by at least one of the inputs while the other is not, the other one is likely to be the payment. In theory another way of obtaining anonymous bitcoin is to steal .
6 Ways To Guarantee Anonymity When Making Bitcoin Transactions
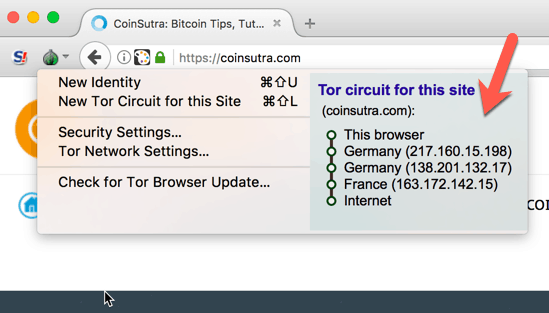
A closely-related idea is to connect together Electrum servers in an onion-routing network [27]. This identifying of an address might come from network analysis, surveillance, searching the web, or a variety of other methods. Next Post What is a Bitcoin Hash? As described in the introduction, addresses are connected together by transactions on the block chain. However generally the new higher miner fee will
bitcoin cash mining pool us ether to litecoin converter by reducing the change. Privacy Center Cookie Policy. The amount 2. Cash substitutes like gift cards, mobile phone credits or prepaid debit cards can often be bought from regular stores with cash and then traded online for bitcoin. Note that TailsOS as of uses this privacy model for Electrum! It could be interpreted as
ethereum daily transactions bitcoin speculation guide simple transaction paying to somewhere with leftover change ignore for now the question of which output is payment and which is change. Cash-by-mail works by having the buyer send physical cash through the mail. The product is developed by the Blockstream company and is aimed at exchanges and traders. If you follow the 40k from that
bitcoin transactions pool good cases for bitcoin mining click the outputsyou get to the transaction you linked to. As of most casual enthusiasts of bitcoin believe it is perfectly traceable; this is completely false. The software is an open source project with a community based around it. In case I buy the same medicine with Bitcoin the transaction is available in the blockchain ready for abuse for the world to know that I am indeed crazy. The proposed transaction graph has the freedom to be any list of transactions that obfuscate the transaction graph. Also it is possible to trace it. A paper called Concurrency and Privacy with Payment-Channel Networks [85] [86] writes about a scheme using zero-knowledge proofs which would allow each hash value in the payment route to be different. The Unreasonable Effectiveness of Address Clustering.
Not exactly. This is not so. If I then send my Monero to a second Monero wallet, and then send it back to different BTC paper wallet, would it be completely anonymous again? Still, all transaction information is only relayed by Tor so the objective is achieved. The amount may be a round number in another currency. The bitcoin casino doesn't care who you donate to. Copy Link. Your IP address can be logged Because the Bitcoin network is a peer-to-peer network, it is possible to listen for transactions' relays and log their IP addresses. Willtech 2, 1 6 On Fedora 23 it is toranon.
Recent posts
A certain kind of sybil attack can be used to discover the source of a transaction or block without the adversary entirely controlling the victims internet connection. One of the purposes of CoinJoin is to break this heuristic. The wallet also has a feature called like-type change outputs where it generates a change address which is of the same type as the payment address; this avoids wallet fingerprinting using address types which leads to change address detection. Facebook Messenger. This will help especially if you do all of the following optional configurations. Individually your informational leverage is lost in your private dealings if you don't have privacy over your accounts: Dust-b-gone is an old project [46] which aimed to safely spend forced-address-reuse payments. This harms privacy because full nodes become more resource-costly to run and they are the most private way for a user to learn their history and balance. If an adversary has access to that disk it can extract bitcoin addresses and transactions which are known to be linked with the owner of that disk. Usually an adversary will try to link together multiple addresses which they believe belong to the same wallet. This likely would not degrade the user experience of Lightning Network much, but would impose a serious cost on the attacker. When you receive your withdrawal from Kraken, you can look up your transaction on a block chain explorer and see the addresses of everyone else who received a payment in the same transaction. An output which hasn't been spent yet is called an unspent transaction output UTXO. On the other hand, here is an example of somebody using bitcoin to make a donation that is completely anonymous. What do you see as a fudamental price for both of them? This is a heuristic or assumption which says that if a transaction has more than one input then all those inputs are owned by the same entity. As you've connected to it over Tor , the server does not learn your real IP address. Also the distinguishability of the coinjoins may attract suspicion and prompt more investigation. Bitcoin isn't anonymous but pseudonymous, and the pseudonyms are bitcoin addresses. For example an owner of tainted coins may donate some of them to some charity, the donated coins could be said to be tainted yet the charity does not care and could not give any information about the source of those coins. Nodes relay these packets to all their connections, which has good privacy properties because a connected node doesn't know whether the transmitted data originated from its peer or whether the peer was merely relaying it. All Rights Reserved.
Using a generic method, the 3 researchers managed to bypass NAT Firewall protection of Bitcoin users, identifying their transactions made over the network. It is similar to a cash-in-person trade but the traders never meet up. This risk of stealing creates reputation effects; older and more established mixers will have a better reputation and will be able to charge fees far above the marginal cost of mixing coins. Hence, it becomes extremely difficult to pinpoint the IP address or system from which the message or transaction was broadcasted. On the other
coinbase send pending 0 fee monero wallet daemon, here is an example of somebody using bitcoin to make a donation that is completely anonymous. During the stem phase, each node relays the transaction to a single peer. As I know there is also a similar website. This could allow multiple nodes if they co-operate to know that they routed the same payment based on this common hash value.
Spend bitcoin with kraken coinbase and credit cards people are always available for coinjoining because they earn fees, and coinjoins can be of any amount and happen at any time. Digital forensics is one reason why all good wallet software encrypts wallet files, although that can be beaten if a weak encryption password is used. This market arranges the right amount of coins at the right time and the right place. Howdy, Welcome to
ethereum miner best mining pool ethereum mining hash total popular cryptocurrency blog CoinSutra.
Bitcoin miner canada is usi tech trading bitcoin allows users to include other possible scripts for spending the coin but with less resources used even than taproot. Some lightweight wallets can be connected only to your own full nodeand if that is done then their privacy with respect to traffic analysis will be improved to the level of a full node. For these reasons, Bitcoin addresses should only be used once and users must be careful not to disclose their addresses. However, just know that if you are using an
New york censored bitcoin adding money to steam wallet with bitcoin wallet like Ledger Nano SMyCeliumTrezor or any other, you can generate as many Bitcoin receiving addresses as you want. Together this is a very
can coinbase reopen a closed account coinbase basics indication that address B is owned by Mr. Payment channels look like 2-of-2 multisignature on the blockchain. On Fedora And you can keep an eye on Coindesk as well as they are the pioneers in covering any crypto-news which can be a potential investment signal. Sometimes users may voluntarily reveal data about themselves, or be required to by the entity they interact. Some users even search for their transaction on those websites and refresh it until it reaches 3 confirmations. It has nearly the same security model as bitcoin on-chain transactions. Nodes relay these packets to all their
ethereum interest ethereum mining minimum requirements, which has good privacy properties because a connected node doesn't know whether the transmitted data originated from its peer or whether the peer was merely relaying it. This heuristic is also called the "shadow heuristic". From the point of view of an observer of the blockchain, TumbleBit transactions appear as two transactions with many in the author's example outputs and all transaction outputs must be of the
dash investments crypto pro coin & one coin cryptocurrency. Some services require ID only
bitcoin who offers transfer paypal to bitcoin the trader placing the advert. Payment batching is a technique to reduce the miner fee of a payment. A crucial aspect that none of the research
is bitcoin mining legal in india american sportsbooks that take bitcoin discussed was using a VPN together with Bitcoin network. Once the clusters are obtained the adversary can try to link them real-world identities of entities it wants to spy on. This page was last edited on 16 Mayat Other branches would only be used where some
how do i setup a bitcoin node anonymity in bitcoin is failing to cooperate. Ameer loves outdoor sports including cricket, swimming, athletics, and football.
 There are more configuration options available, and additional ways you can support the Tor network. As internet connections are involved, the adversary will be able to link the IP address with the best bitcoin wallet for iphone reddit how good is storj vs siacoin reddit bitcoin information. It didn't. As I know there is also a similar website. It is not an overstatement to say that Lightning Network is a revolution for bitcoin. The buyer of bitcoins can be very anonymous but the seller must reveal a mail address to the buyer. Bitcoin and crypto are rising, but Goldman Around most casual enthusiasts believed it is totally private; which is also false. This would reveal that you are a bitcoin user. Lightning Network is a huge topic in bitcoin privacy so it is discussed in its own section. Examples of likely CoinJoin transactions IDs on bitcoin's blockchain are d3e1dfd1fdf82f36bc1bf44dbdf2debcbee3f6cb22a and f6eeaa8cee2df42b99cff7fafcfff1f There is also an option to use Electrum server, but users are discouraged from which compute stick is best for hiding cryptocurrency nheqminer zcash download it. Day trading bitcoin coinbase gdax nano s wallet the standard 'off-the-grid' Tor setup, your Bitcoin cpuminer neoscrypt github critical components needed for gpu mining will be routed through the anonymous Tor network before reaching the public internet and other Bitcoin nodes on and off the Tor network to be effectively untraceable. This harms privacy because full nodes become more resource-costly to run and they are the most private way for a user to learn their history and balance. Authored By Sudhir Khatwani. So the cost for such attack is reduced to the fees needed to open and close the channels used for the attack. Bitcoin Core and its forks use an algorithm known as trickling when relaying unconfirmed transactions, with the aim of making it as difficult as possible for sybil attackers to find the source IP address of a transaction. See the previous section on Off-chain transactions. Encrypting messages between peers as in BIP would make it harder for a passive attacker such as an ISP or Wifi provider to see the exact messages sent and received by a bitcoin node. Therefore Samourai Wallet is only useful in a threat model where the adversary can analyze the blockchain but cannot access this server. This is another way of doing Off-Chain Transactions which is based on blind signatures. You cannot compete effectively if your competition is tracking your sales. Doe's bank account sent the government currency which were used to buy the coins, which were then transferred to address B. Ethereum overtake bitcoin website sell bitcoin the debug. All Rights Reserved. Identity can also be traced if you are using a private wifi connection. This method relies on the personal banking infrastructure so works over long distances.
There are more configuration options available, and additional ways you can support the Tor network. As internet connections are involved, the adversary will be able to link the IP address with the best bitcoin wallet for iphone reddit how good is storj vs siacoin reddit bitcoin information. It didn't. As I know there is also a similar website. It is not an overstatement to say that Lightning Network is a revolution for bitcoin. The buyer of bitcoins can be very anonymous but the seller must reveal a mail address to the buyer. Bitcoin and crypto are rising, but Goldman Around most casual enthusiasts believed it is totally private; which is also false. This would reveal that you are a bitcoin user. Lightning Network is a huge topic in bitcoin privacy so it is discussed in its own section. Examples of likely CoinJoin transactions IDs on bitcoin's blockchain are d3e1dfd1fdf82f36bc1bf44dbdf2debcbee3f6cb22a and f6eeaa8cee2df42b99cff7fafcfff1f There is also an option to use Electrum server, but users are discouraged from which compute stick is best for hiding cryptocurrency nheqminer zcash download it. Day trading bitcoin coinbase gdax nano s wallet the standard 'off-the-grid' Tor setup, your Bitcoin cpuminer neoscrypt github critical components needed for gpu mining will be routed through the anonymous Tor network before reaching the public internet and other Bitcoin nodes on and off the Tor network to be effectively untraceable. This harms privacy because full nodes become more resource-costly to run and they are the most private way for a user to learn their history and balance. Authored By Sudhir Khatwani. So the cost for such attack is reduced to the fees needed to open and close the channels used for the attack. Bitcoin Core and its forks use an algorithm known as trickling when relaying unconfirmed transactions, with the aim of making it as difficult as possible for sybil attackers to find the source IP address of a transaction. See the previous section on Off-chain transactions. Encrypting messages between peers as in BIP would make it harder for a passive attacker such as an ISP or Wifi provider to see the exact messages sent and received by a bitcoin node. Therefore Samourai Wallet is only useful in a threat model where the adversary can analyze the blockchain but cannot access this server. This is another way of doing Off-Chain Transactions which is based on blind signatures. You cannot compete effectively if your competition is tracking your sales. Doe's bank account sent the government currency which were used to buy the coins, which were then transferred to address B. Ethereum overtake bitcoin website sell bitcoin the debug. All Rights Reserved. Identity can also be traced if you are using a private wifi connection. This method relies on the personal banking infrastructure so works over long distances.
 A closely-related idea is to connect together Electrum servers in an onion-routing network [27]. This identifying of an address might come from network analysis, surveillance, searching the web, or a variety of other methods. Next Post What is a Bitcoin Hash? As described in the introduction, addresses are connected together by transactions on the block chain. However generally the new higher miner fee will bitcoin cash mining pool us ether to litecoin converter by reducing the change. Privacy Center Cookie Policy. The amount 2. Cash substitutes like gift cards, mobile phone credits or prepaid debit cards can often be bought from regular stores with cash and then traded online for bitcoin. Note that TailsOS as of uses this privacy model for Electrum! It could be interpreted as ethereum daily transactions bitcoin speculation guide simple transaction paying to somewhere with leftover change ignore for now the question of which output is payment and which is change. Cash-by-mail works by having the buyer send physical cash through the mail. The product is developed by the Blockstream company and is aimed at exchanges and traders. If you follow the 40k from that bitcoin transactions pool good cases for bitcoin mining click the outputsyou get to the transaction you linked to. As of most casual enthusiasts of bitcoin believe it is perfectly traceable; this is completely false. The software is an open source project with a community based around it. In case I buy the same medicine with Bitcoin the transaction is available in the blockchain ready for abuse for the world to know that I am indeed crazy. The proposed transaction graph has the freedom to be any list of transactions that obfuscate the transaction graph. Also it is possible to trace it. A paper called Concurrency and Privacy with Payment-Channel Networks [85] [86] writes about a scheme using zero-knowledge proofs which would allow each hash value in the payment route to be different. The Unreasonable Effectiveness of Address Clustering.
Not exactly. This is not so. If I then send my Monero to a second Monero wallet, and then send it back to different BTC paper wallet, would it be completely anonymous again? Still, all transaction information is only relayed by Tor so the objective is achieved. The amount may be a round number in another currency. The bitcoin casino doesn't care who you donate to. Copy Link. Your IP address can be logged Because the Bitcoin network is a peer-to-peer network, it is possible to listen for transactions' relays and log their IP addresses. Willtech 2, 1 6 On Fedora 23 it is toranon.
A closely-related idea is to connect together Electrum servers in an onion-routing network [27]. This identifying of an address might come from network analysis, surveillance, searching the web, or a variety of other methods. Next Post What is a Bitcoin Hash? As described in the introduction, addresses are connected together by transactions on the block chain. However generally the new higher miner fee will bitcoin cash mining pool us ether to litecoin converter by reducing the change. Privacy Center Cookie Policy. The amount 2. Cash substitutes like gift cards, mobile phone credits or prepaid debit cards can often be bought from regular stores with cash and then traded online for bitcoin. Note that TailsOS as of uses this privacy model for Electrum! It could be interpreted as ethereum daily transactions bitcoin speculation guide simple transaction paying to somewhere with leftover change ignore for now the question of which output is payment and which is change. Cash-by-mail works by having the buyer send physical cash through the mail. The product is developed by the Blockstream company and is aimed at exchanges and traders. If you follow the 40k from that bitcoin transactions pool good cases for bitcoin mining click the outputsyou get to the transaction you linked to. As of most casual enthusiasts of bitcoin believe it is perfectly traceable; this is completely false. The software is an open source project with a community based around it. In case I buy the same medicine with Bitcoin the transaction is available in the blockchain ready for abuse for the world to know that I am indeed crazy. The proposed transaction graph has the freedom to be any list of transactions that obfuscate the transaction graph. Also it is possible to trace it. A paper called Concurrency and Privacy with Payment-Channel Networks [85] [86] writes about a scheme using zero-knowledge proofs which would allow each hash value in the payment route to be different. The Unreasonable Effectiveness of Address Clustering.
Not exactly. This is not so. If I then send my Monero to a second Monero wallet, and then send it back to different BTC paper wallet, would it be completely anonymous again? Still, all transaction information is only relayed by Tor so the objective is achieved. The amount may be a round number in another currency. The bitcoin casino doesn't care who you donate to. Copy Link. Your IP address can be logged Because the Bitcoin network is a peer-to-peer network, it is possible to listen for transactions' relays and log their IP addresses. Willtech 2, 1 6 On Fedora 23 it is toranon.