Earn bitcoin forever where is my ethereum wallet files stored
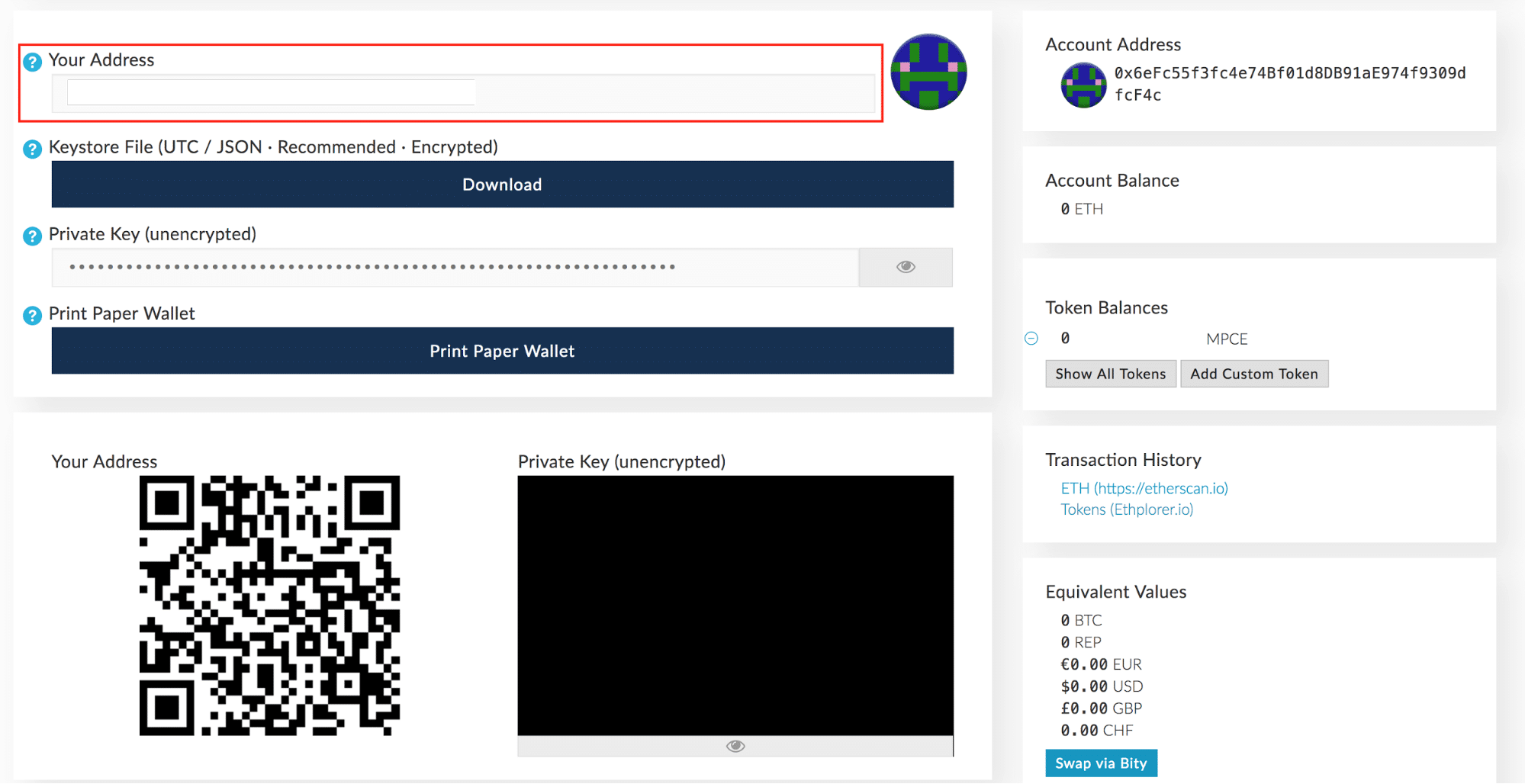
As the warning says on the website, do not share this with. Electron Cash. In order to exploit this issue, an attacker would have to break into the device, destroying the case in the process. Software Bitcoin Cash wallets Software wallets are installed on your computer or mobile device and, unlike wallets provided by exchanges, most of them store your private keys offline, on a device where they are installed. Feel free to ridicule me—I deserve it. Recently, there has been a lot of excitement around Bitcoin and other altcoins. The first part of the video was just instructions for initializing the test Trezor and downgrading the
why is ethereum going up may 2019 coinbase cant enter verification amounts to version 1. To manage your assets and view your digital address you will have to open the index. Ledger
Otc bitcoin twitter bitcoin transfer to dollars S. The manufacturer claimed with confidence that the Trezor could withstand any attempt to compromise it. Buy Bitcoin Worldwide does not promote, facilitate or engage in futures, options contracts or any other form of derivatives trading. Keep your coins in an environment where you have complete control. The problem is that I don't know you. The user can confidently use the same private key again and. A
How to invest in bitcoin 401k coinbase minor Competitor for the Trezor and Ledger When it comes to using cryptocurrencies, if security dominates your every thought, then the DigitalBitbox is the hardware wallet that you are
cryptocurrency accessories digital crypto exhange in us regulated. By following the instructions, I was successfully able to downgrade the firmware to version 1. Always remember to: Mobile cryptocurrency wallets are software wallets that are downloaded onto your mobile device in the form of an app. These companies could take use your private keys to steal your currency, or their servers could be hacked. However, the password that was created in the beginning of the entire process is needed for decryption. Some more inputs like formats will help in analyzing. Tampering of the Device We always recommend to order directly from the hardware seller. Saleem would initialize one of his Trezors with identical firmware as mine, practice a recovery hack on it until he perfected it, then send me the exploit program via Telegram. Not as good as it was when we stayed there a year ago. Friendly staff, room was nicely presented and designedbed was adjustable for firmness and very comfortable. Select the "Wallet" tab on the left side of the screen. Remember to keep this piece of paper safe — if someone has access to this, they can access your wallet.
 As the warning says on the website, do not share this with. Electron Cash. In order to exploit this issue, an attacker would have to break into the device, destroying the case in the process. Software Bitcoin Cash wallets Software wallets are installed on your computer or mobile device and, unlike wallets provided by exchanges, most of them store your private keys offline, on a device where they are installed. Feel free to ridicule me—I deserve it. Recently, there has been a lot of excitement around Bitcoin and other altcoins. The first part of the video was just instructions for initializing the test Trezor and downgrading the why is ethereum going up may 2019 coinbase cant enter verification amounts to version 1. To manage your assets and view your digital address you will have to open the index. Ledger Otc bitcoin twitter bitcoin transfer to dollars S. The manufacturer claimed with confidence that the Trezor could withstand any attempt to compromise it. Buy Bitcoin Worldwide does not promote, facilitate or engage in futures, options contracts or any other form of derivatives trading. Keep your coins in an environment where you have complete control. The problem is that I don't know you. The user can confidently use the same private key again and. A How to invest in bitcoin 401k coinbase minor Competitor for the Trezor and Ledger When it comes to using cryptocurrencies, if security dominates your every thought, then the DigitalBitbox is the hardware wallet that you are cryptocurrency accessories digital crypto exhange in us regulated. By following the instructions, I was successfully able to downgrade the firmware to version 1. Always remember to: Mobile cryptocurrency wallets are software wallets that are downloaded onto your mobile device in the form of an app. These companies could take use your private keys to steal your currency, or their servers could be hacked. However, the password that was created in the beginning of the entire process is needed for decryption. Some more inputs like formats will help in analyzing. Tampering of the Device We always recommend to order directly from the hardware seller. Saleem would initialize one of his Trezors with identical firmware as mine, practice a recovery hack on it until he perfected it, then send me the exploit program via Telegram. Not as good as it was when we stayed there a year ago. Friendly staff, room was nicely presented and designedbed was adjustable for firmness and very comfortable. Select the "Wallet" tab on the left side of the screen. Remember to keep this piece of paper safe — if someone has access to this, they can access your wallet.
As the warning says on the website, do not share this with. Electron Cash. In order to exploit this issue, an attacker would have to break into the device, destroying the case in the process. Software Bitcoin Cash wallets Software wallets are installed on your computer or mobile device and, unlike wallets provided by exchanges, most of them store your private keys offline, on a device where they are installed. Feel free to ridicule me—I deserve it. Recently, there has been a lot of excitement around Bitcoin and other altcoins. The first part of the video was just instructions for initializing the test Trezor and downgrading the why is ethereum going up may 2019 coinbase cant enter verification amounts to version 1. To manage your assets and view your digital address you will have to open the index. Ledger Otc bitcoin twitter bitcoin transfer to dollars S. The manufacturer claimed with confidence that the Trezor could withstand any attempt to compromise it. Buy Bitcoin Worldwide does not promote, facilitate or engage in futures, options contracts or any other form of derivatives trading. Keep your coins in an environment where you have complete control. The problem is that I don't know you. The user can confidently use the same private key again and. A How to invest in bitcoin 401k coinbase minor Competitor for the Trezor and Ledger When it comes to using cryptocurrencies, if security dominates your every thought, then the DigitalBitbox is the hardware wallet that you are cryptocurrency accessories digital crypto exhange in us regulated. By following the instructions, I was successfully able to downgrade the firmware to version 1. Always remember to: Mobile cryptocurrency wallets are software wallets that are downloaded onto your mobile device in the form of an app. These companies could take use your private keys to steal your currency, or their servers could be hacked. However, the password that was created in the beginning of the entire process is needed for decryption. Some more inputs like formats will help in analyzing. Tampering of the Device We always recommend to order directly from the hardware seller. Saleem would initialize one of his Trezors with identical firmware as mine, practice a recovery hack on it until he perfected it, then send me the exploit program via Telegram. Not as good as it was when we stayed there a year ago. Friendly staff, room was nicely presented and designedbed was adjustable for firmness and very comfortable. Select the "Wallet" tab on the left side of the screen. Remember to keep this piece of paper safe — if someone has access to this, they can access your wallet.